Can You Have Fun with Ransomware?
Depending on who you ask, the prevailing opinion is that there’s minimal common ground between a bank and a casino. However, they do share one significant similarity: the substantial inflow and outflow of money—typically more inflow, as the house invariably has the upper hand *ahem*. Would it surprise you to learn that, over the past few months, these two establishments have acquired another commonality: Ransomware attacks’ targets.
My Reflections on the Cybersecurity Landscape
Not too long ago, two significant attacks captured headlines around the world.:
- BSI, a large bank in Indonesia was attacked by a ransomware cyber criminal group Lockbit 3.0 with 1.5 terabytes of data acquired. ”This massive breach comprises sensitive personal information belonging to a staggering 15 million customers and staff members of the bank.” – Indonesia Business Post
- MGM Resorts Group’s ransomware attack must have cost them considerably every minute the system was down, given that.”In the quarter that ended on June 30, the company reported that its Las Vegas Strip properties generated revenue of $1.2 billion just from hotel rooms and casinos. Based on those figures, MGM’s Vegas Strip properties bring in more than $13 million per day in revenue.” – Forbes
As a substantial collective that depends on its employees’ productivity to drive revenue, dealing with such attacks can be slightly troublesome. What is the approach then? Essentially, you consider solutions to ward off malware. You continuously remind and educate your staff, emphasizing repeatedly the risks of clicking on dubious attachments. You conduct phishing drills and celebrate when 90% of your team can identify phishing scams from afar, only to find yourself dealing with a ransomware attack eventually. So, does it make one ponder the efficacy of it all? Should securing the network from ransomware not be a priority?
Any CISO with a modicum of self-respect knows the answer. Those who don’t might find themselves in discreet discussions with the Board of Directors, interpreting the ‘Bad Leaver’ clause in their contracts. The unequivocal answer is, ‘Yes, we must unequivocally exert every effort to counteract malware and likely allocate more resources towards it!’
But I want to dig a bit deeper. I’ve always advocated for being paranoid and always assuming you will be hacked. So with that, I want to outline a few things to think about – a thought experiment if you will – of what to do when you get attacked by ransomware.
What exactly is Ransomware?
Ransomware is a type of malware that sweeps through your network infecting all servers and workstations. It garbles and locks all data on the network rendering the devices unusable. After it locks the data, the machine boots to a message that informs you to deposit an amount of cryptocurrency (ranging from tens of thousands to tens of millions depending on how big the attackers see your group as) to get an unlock key – essentially holding your productivity for ransom.
According to Statista’s report on the number of ransomware attempts worldwide, in 2022, there were 493.33 million ransomware attempts that were reported by organisations around the world.
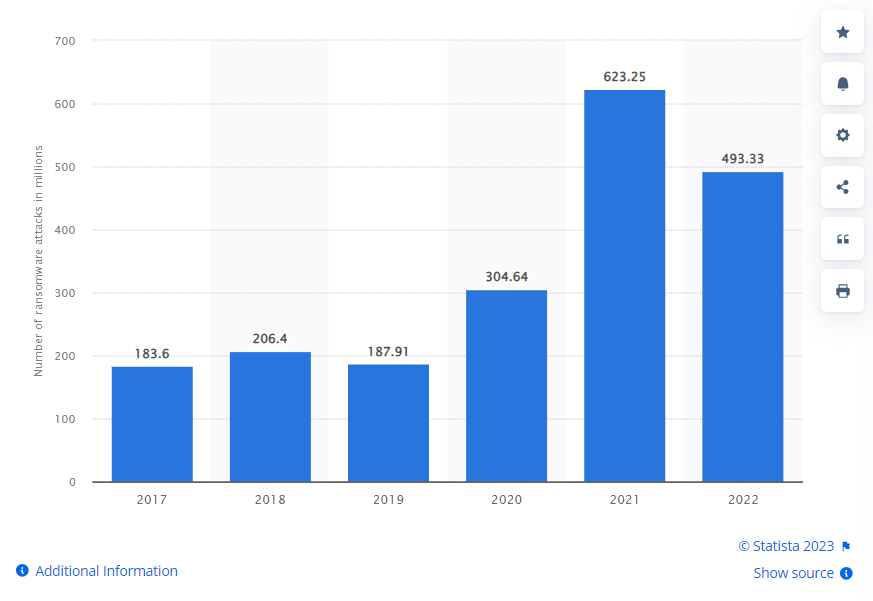 Annual number of ransomware attempts worldwide from 2017 to 2022 (in millions)
Annual number of ransomware attempts worldwide from 2017 to 2022 (in millions)
Organisations experiencing cyber attacks incur not only the financial burden of retrieving their own data but also suffer reputational damage once the incident becomes public knowledge.
So, Here Are Some Thoughts I Have for Preparing Ourselves
1. First Things
Have a plan. Cancel your meetings, switch off your phone, and think about the scenario. Build a plan that you will stick to when it comes to a disaster.
Priority number one should be the restoration of normal operations. You need to reinstate your business activities promptly. Any downtime equates to financial loss, and it won’t be long before you have individuals impatiently inquiring about the restoration time frame. Formulate a practical plan, emphasising clear communication, and remain committed to it.
2. Backups
It goes without saying that backups are important. For servers yes, but a ransomware attack will also target all your users. Yes, all! The call centre, the logistics department, the HR department, operations, admin, IT, all.
Thus, maintaining backups for data on workstations is crucial. Close, careful attention is required in managing how you handle and test your backups. Having current backups—almost in real time—relieves the anxiety over potential data loss. With them, restoration from a backup should enable you to resume your work seamlessly.
3. Who to Bring Online First?
This involves knowing your business and understanding which department has to absolutely always stay online and productive. By this I mean, you will have to send your First Responder team to re-install all the workstations in that department. I would start asking myself these questions to strategize the situation:
- How can you reinstall Windows when your remote Windows image server is also compromised?
- Do you have access to a USB or CD for this purpose?
- Is your team well-practised in executing such tasks?
- Do they have a leaderboard of the “Fastest Windows and Data Restorer”?
4. Do You Have a First Responder Team?
Unless you’re in the enviable position to have a vast army of tech team, you’re going to find yourself limited in output. You’re quite likely to have more workstations and servers to restore than you have able people. This is when it becomes essential to expand your reach to other teams and identify the technologically adept ones to “volunteer” as part of a first responder team. Cultivate a group of first responders from non-tech and non-infosec teams, train them, and ensure they rehearse for the inevitable day when they’ll be needed to scurry around the office restoring workstations. Undertaking this alone isn’t viable. Without adequate preparation, you’ll find yourself overwhelmed and ineffective, unable to respond promptly and efficiently.
5. Automate as Much as Possible
When the moment arrives to reactivate your servers, manually reimaging servers with precise configurations and services can be time-consuming. Thus, the optimal time to understand how to best automate builds and deployments of your servers is when you’re not under attack. This enables your team to initiate a rebuild, leave it, and the server self-activates. Automating your DevOps and possessing a solid CI/CD pipeline is invaluable, not merely in the event of a ransomware attack but also during outages.
6. Think about Your Customers
I know this goes without saying, but restoring all your data and getting back online successfully and quickly isn’t always the goal. In BSI’s case, allegedly millions of users’ data was stolen. The group who attacked them not only wanted a ransom to restore their network, but also threatened to release all this data on the dark web if the ransom wasn’t paid. This discussion is another rabbit hole that I won’t go into at this point, but it greatly influences your decision to negotiate and pay the ransom. There are ways to mitigate this by collecting the bare minimum of personally identifiable information from your users, but in some cases, you need that data and so you should be mindful of how to safeguard it.
7. Practice is Overlooked
It took me a long time to come around to why a Business Continuity Plan needed to be practised. I thought it was a waste of time. It isn’t. Practising and knowing what you do when it’s gametime is so absolutely invaluable. Training and repetition is what makes some of the US’s elite military units…erm… elite. They drill incessantly so that when they do it for real, nothing is new.
I remember once taking a flight from San Francisco to Singapore where the airline staff were conducting such a test. The scenario was that they were to assume all online systems were down and were to plan to get passengers checked in and on their way as quickly as possible. While it did inconvenience passengers, I must admit I was genuinely impressed by how the airline and its staff managed this scenario. I received a handwritten boarding pass, but I was on my way with a reasonable delay and didn’t miss my flight.
So, let’s practise all these we discussed:
- Backing up data and restoring it – Restoring is the more important part. Having petabytes of backups that can’t be restored isn’t helpful.
- Rebuilding Workstations and Servers – Practise how your team will rebuild all the workstations in a department. You can start with a subset, but the bigger you go, the better.
- Constantly test your plan on a smaller scale, then on a big scale – You won’t know how good your plan is until you practise it and figure out sticking points in your process. Practise the plan, then refine the plan, then practise again.
8. Lastly, go out there and have fun!
What good is all this if you can’t sit in your room while everything around you is burning and tell yourself that this is fine? Ransomware can happen to anyone, big or small. By all means figure out how to prevent it, but do yourself a favour and also think about what you will do when you do get hit. I’ve touched on only a very few points in this post, but if you like to discuss these in more depth, feel free to reach out! I can talk your ear off for most of the day.
About The Author
Sheran Gunasekera is a security researcher and software developer. He is co-founder and Director of Research for Madison Technologies, a software development company in Singapore, where he advises the in-house engineering team in both personal computer and mobile device security. Sheran’s foray into mobile security began in 2009 when he started with BlackBerry security research. Since then, he has been in leadership roles in both engineering and security at several startups in Asia including GOJEK, the on-demand multi-service app that is now publicly listed.
| Contact us today! We’re open for discussions. |






